Verificación de flooding inter VLAN
Fecha: 9 de septiembre del 2014 Clase: CCNA Security
Escenario
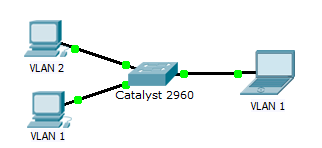
Este laboratorio intenta demostrar, que si generando una inundación en la tabla de MAC address de un switch,
es afectada la VLAN donde se genera o la tabla entera.
Según la currícula de CCNASec, esta inundación de tráfico no afecta las otras VLANs.
A verificarlo…
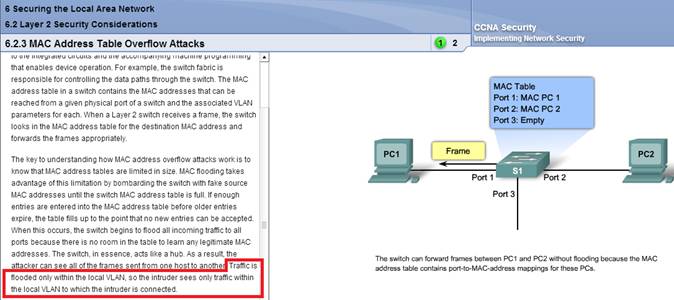
The key to understanding how MAC address overflow attacks work is to know that MAC address tables are limited in size.
MAC flooding takes advantage of this limitation by bombarding the switch with fake source MAC addresses until the switch
MAC address table is full. If enough entries are entered into the MAC address table before older entries expire, the table
fills up to the point that no new entries can be accepted. When this occurs, the switch begins to flood all incoming traffic to
all ports because there is no room in the table to learn any legitimate MAC addresses. The switch, in essence, acts like a hub.
As a result, the attacker can
see all of the frames sent from one host to another. Traffic is flooded only within the local VLAN,
so the intruder sees only traffic within the local VLAN to which the intruder is connected.
Verificación inicial:
Cisco_2960>show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gi0/1, Gi0/2
2 VLAN0002 active Fa0/1, Fa0/2
3 VLAN0003 active Fa0/3, Fa0/4
4 VLAN0004 active Fa0/5, Fa0/6
5 VLAN0005 active Fa0/7, Fa0/8
---resumido---
Cisco_2960>
Cisco_2960>sh mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
All 0100.0ccc.cccc STATIC CPU
---resumido---
All ffff.ffff.ffff STATIC CPU
1 001b.387e.f171 DYNAMIC
Fa0/24
1 54be.f757.effb DYNAMIC Fa0/23
2 54be.f757.f30e DYNAMIC
Fa0/1
Total Mac Addresses for this criterion: 28
Cisco_2960>
Durante la inundación de la tabla de MAC (desde el port Fa0/24):
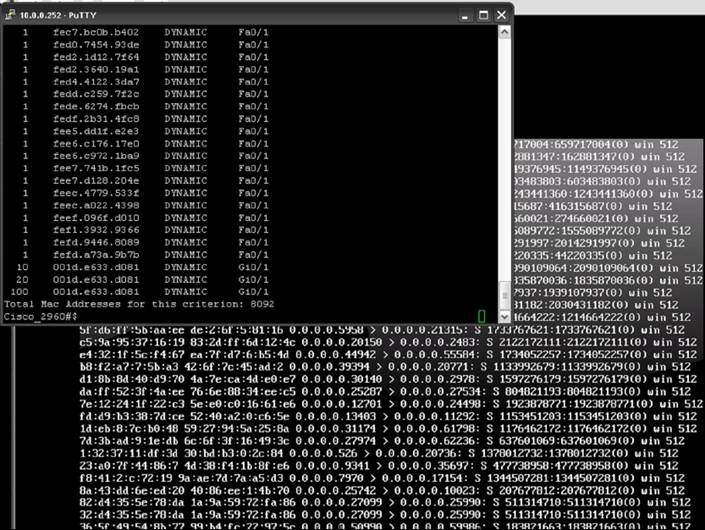
Cisco_2960>sh mac address-table | incl Total
Total Mac Addresses for this criterion: 8092
Cisco_2960>sh proc | incl CPU (no tiene demasiado impacto en el procesador)
CPU utilization for five seconds: 35%/2%; one minute: 69%; five minutes: 36%
Cisco_2960>
En la PC de la VLAN atacada (vlan1, port Fa0/23):
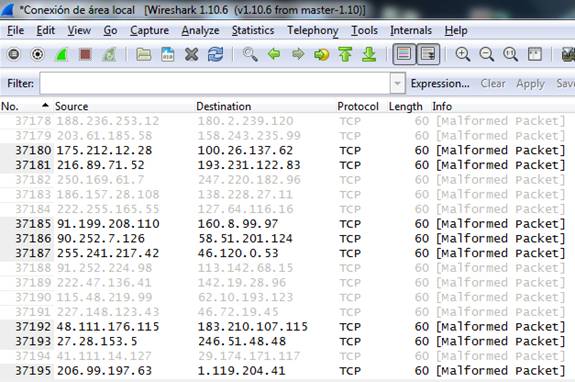
En la PC de la VLAN no atacada (vlan 2, port Fa0/1):
Verificamos que la tabla de mac address, al llenarse, realiza flooding sólo en la VLAN donde se inyecta el tráfico.
Se puede observar que el spanning tree y el CDP se desactivaron para realizar una captura de tráfico limpia, sólo
se muestra el tráfico generado por el ataque.
Si bien estaba en la currícula, hay que ver para creer.
(2014) Sensei, does the
packet storm comes from the cloud ?
Rosario, Argentina