Trabajo práctico final CCNASecurity 2016
Fecha: 30 de noviembre del 2016 Resuelto por: Rodrigo Flores, Marcos Leiva
Este trabajo se presentó a los alumnos presentes en la clase como desafío para la finalización del curso CCNASec 2016.
El mismo hace incapié en la importancia de documentar las topologías que nos podríamos hacer cargo en un futuro, la
topología hay que imaginarla a partir de los names y objetos, sus IP e interfaces correspondientes en el firewall, así
como los peers VPN y los NAT.
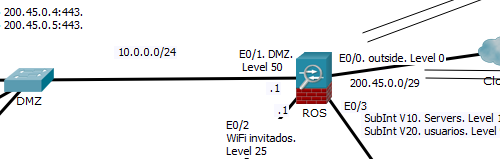
Escenario
A partir de la configuración de un Cisco ASA 5510, relevar las caracterísiticas de la misma, diseñar el contexto físico del mismo
y realizar en Packet Tracer una topología tentativa (sin implementar configuraciones) agregando la mayor cantidad de detalles
posibles en los anotadores (protocolos, IP, etc).
Configuración del ASA:
FW_Rosario#sh runn
: Saved
:
: Serial Number: JMX1855914A
: Hardware:
ASA5510, 1024 MB RAM, CPU Pentium 4 Celeron 1600 MHz
:
ASA Version 8.4(7)30
!
hostname FW_Rosario
enable password hGsHQ2/QA2fD6C4Z encrypted
names
name 192.168.10.10 SRVROS10
name 192.168.10.11 SRVROS11
name 192.168.10.12 SRVROS12
name 192.168.10.13 SRVROS13
name 192.168.10.14 SRVROS14
name 192.168.10.100 SWROS100
name 192.168.10.101 SWROS101
name 192.168.10.102 SWROS102
!
interface Ethernet0/0
description OUTSIDE
nameif
outside
security-level 0
ip
address 200.45.0.1 255.255.255.248 standby 200.45.0.2
!
interface Ethernet0/1
description DMZ
nameif
dmz
security-level
50
ip
address 10.0.0.1 255.255.255.0 standby 10.0.0.2
!
interface Ethernet0/2
description WiFI invitados
nameif
invitados
security-level 25
ip
address 172.16.0.1 255.255.255.0 standby 172.16.0.2
!
interface Ethernet0/3
no
nameif
no
security-level
no ip
address
!
interface Ethernet0/3.10
description Inside servers
vlan 10
nameif
servers
security-level 100
ip
address 192.168.10.1 255.255.255.0 standby 192.168.10.2
!
interface Ethernet0/3.20
description Inside usuarios
vlan 20
nameif
usuarios
security-level 90
ip
address 192.168.20.1 255.255.255.0 standby 192.168.20.2
!
interface Management0/0
description LAN/STATE Failover Interface
management-only
!
boot system disk0:/asa847-30-k8.bin
clock timezone AR -3
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj-SRVROS10
host
192.168.10.10
object network obj-SRVROS11
host
192.168.10.11
object network obj-SRVROS12
host
192.168.10.12
object network obj-SRVROS13
host
192.168.10.13
object network obj-SRVDMZ10
host
10.0.0.10
object network obj-SRVDMZ11
host
10.0.0.11
object network obj-SRVDMZNAT
host
10.0.0.254
object service obj-tcp-source-eq-80
service
tcp source eq www
object service obj-tcp-source-eq-443
service
tcp source eq https
object service obj-tcp-source-eq-1433
service
tcp source eq 1433
object service obj-tcp-source-eq-450
service
tcp source eq 450
object network obj-SERVERS
subnet
192.168.10.0 255.255.255.0
object network obj-USUARIOS
subnet 192.168.20.0
255.255.255.0
object network obj-DMZ
subnet
10.0.0.0 255.255.255.0
object network obj-INVITADOS
subnet
172.16.0.0 255.255.255.0
object network obj-200.45.0.1
host
200.45.0.1
object network obj-200.45.0.2
host
200.45.0.2
object network obj-200.45.0.3
host
200.45.0.3
object network obj-200.45.0.4
host
200.45.0.4
object network obj-200.45.0.5
host
200.45.0.5
object network obj-200.45.0.6
host
200.45.0.6
object-group network obj-ROSARIO
network-object 192.168.10.0 255.255.255.0
network-object
192.168.20.0 255.255.240.0
object-group network obj-CORDOBA
network-object 192.168.100.0 255.255.255.0
object-group network obj-TUCUMAN
network-object 192.168.110.0 255.255.255.0
access-list ACL-FROM-USUARIOS extended permit
tcp object-group obj-ROSARIO any eq 80
access-list ACL-FROM-USUARIOS extended permit
tcp object-group obj-ROSARIO any eq 443
access-list ACL-FROM-USUARIOS extended permit
udp object-group obj-ROSARIO host 8.8.8.8 eq 53
access-list ACL-FROM-USUARIOS extended permit
tcp object-group obj-ROSARIO object-group obj-DMZ eq 3389
access-list ACL-FROM-USUARIOS extended permit
tcp object-group obj-ROSARIO object-group obj-DMZ eq 443
access-list ACL-FROM-USUARIOS extended permit
ip object-group obj-ROSARIO object-group
obj-CORDOBA
access-list ACL-FROM-USUARIOS extended permit
ip object-group obj-ROSARIO object-group
obj-TUCUMAN
access-list ACL-FROM-DMZ extended permit tcp
object-group obj-DMZ object-group obj-SRVROS10 eq 1433
access-list ACL-FROM-DMZ extended permit tcp
object-group obj-DMZ object-group obj-SRVROS11 eq 1433
access-list ACL-FROM-DMZ extended permit tcp
object-group obj-DMZ any eq 80
access-list ACL-FROM-DMZ extended permit tcp
object-group obj-DMZ any eq 443
access-list ACL-FROM-DMZ extended permit udp
object-group obj-DMZ any eq 53
access-list ACL-FROM-DMZ extended permit tcp
object-group obj-DMZ any eq 450
access-list ACL-FROM-INVITADOS extended permit
tcp object-group obj-INVITADOS any eq 80
access-list ACL-FROM-INVITADOS extended permit
tcp object-group obj-INVITADOS any eq 443
access-list ACL-FROM-INVITADOS extended permit
udp object-group obj-INVITADOS any eq 53
access-list ACL-FROM-SERVERS extended permit
tcp object-group obj-SERVERS any eq 80
access-list ACL-FROM-SERVERS extended permit tcp
object-group obj-SERVERS any eq 443
access-list ACL-FROM-SERVERS extended permit
udp object-group obj-SERVERS any eq 53
access-list ACL-FROM-SERVERS extended permit
tcp object-group obj-SERVERS object-group obj-DMZ eq 1433
access-list ACL-FROM-OUTSIDE extended permit
tcp object-group obj-SRVDMZ10 any eq 443
access-list ACL-FROM-OUTSIDE extended permit
tcp object-group obj-SRVDMZ11 any eq 443
access-list VPN-ROSARIO-CORDOBA extended permit
ip object-group obj-ROSARIO object-group
obj-CORDOBA
access-list VPN-ROSARIO-TUCUMAN extended permit
ip object-group obj-ROSARIO object-group
obj-TUCUMAN
logging enable
logging timestamp
logging buffer-size 256000
logging trap errors
logging host 192.168.10.12
logging asdm informational
flow-export destination inside 192.168.10.14
9996
mtu inside 1500
mtu dmz 1500
mtu outside 1500
mtu tlsptp 1500
mtu tlsmerval 1500
failover
failover lan unit secondary
failover lan interface heartbeat Management0/0
failover polltime interface 2 holdtime 10
failover replication http
failover mac address Ethernet0/0 d48c.b5c9.51fc
0013.c480.a45c
failover mac address Ethernet0/1 d48c.b5c9.51fd
0013.c480.a45d
failover mac address Ethernet0/2 d48c.b5c9.51fe
0013.c480.a45e
failover mac address Ethernet0/3 d48c.b5c9.51ff
0013.c480.a45f
failover link heartbeat Management0/0
failover interface ip heartbeat 10.10.10.1
255.255.255.0 standby 10.10.10.2
icmp unreachable rate-limit 1 burst-size 1
icmp permit 192.168.0.0 255.255.0.0 inside
asdm image disk0:/asdm-752-153.bin
nat (dmz,outside) source static obj-SRVDMZ10
obj-200.45.0.4 service obj-tcp-source-eq-443 obj-tcp-source-eq-443
nat (dmz,outside) source static obj-SRVDMZ11
obj-200.45.0.5 service obj-tcp-source-eq-443 obj-tcp-source-eq-443
nat (servers,dmz) source static obj-SRVROS14
obj-SRVDMZNAT service obj-tcp-source-eq-1433 obj-tcp-source-eq-1433
nat (servers,dmz) source static obj-SRVROS14
obj-SRVDMZNAT service obj-tcp-source-eq-450 obj-tcp-source-eq-450
nat (servers,outside) source static obj-SERVERS
obj-SERVERS destination static obj-CORDOBA obj-CORDOBA
nat (servers,outside) source static obj-SERVERS
obj-SERVERS destination static obj-TUCUMAN obj-TUCUMAN
nat (usuarios,outside) source static
obj-USUARIOS obj- USUARIOS destination static obj-CORDOBA obj-CORDOBA
nat (usuarios,outside) source static
obj-USUARIOS obj- USUARIOS destination static obj-TUCUMAN obj-TUCUMAN
nat (dmz,outside) source dynamic obj-DMZ
obj-200.45.0.4
nat (servers,outside) source dynamic obj-DMZ
interface
nat (servers,dmz) source dynamic obj-SERVERS
obj-SRVDMZNAT
nat (inside,outside) source dynamic obj-ROSARIO
obj-200.45.0.5
nat (servers,dmz) source dynamic obj-USUARIOS
obj-SRVDMZNAT
nat (invitados,outside) source dynamic
obj-INVITADOS obj-200.45.0.3
access-group ACL-FROM-SERVERS in interface
servers
access-group ACL-FROM-USUARIOS in interface
usuarios
access-group ACL-FROM-INVITADOS in interface
invitados
access-group ACL-FROM-DMZ in interface dmz
access-group ACL-FROM-OUTSIDE in interface
outside
route outside 0.0.0.0 0.0.0.0 200.0.0.6 (aquí hay un error de tipeo del documento, el próximo salto debe ser 200.45.0.6,
timeout xlate 1:00:00 ya que las IP 1,2,3,4 y 5 se utilizan en el ASA, visto de otra manera podemos utilizarlo
timeout pat-xlate 0:00:30 como trampa para ver si se prestó atención o no ;-)
timeout conn 1:00:00 half-closed 0:10:00 udp
0:02:00 icmp 0:00:02
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
http server enable
http 192.168.20.123 255.255.255.255 usuarios
snmp-server host inside 192.168.10.12 community
Ro5ar1o version 2c
snmp-server location FW-ROSARIO
snmp-server contact SISTEMAS
snmp-server community Ro5ar1o
snmp-server enable traps snmp authentication
linkup linkdown coldstart
snmp-server enable traps syslog
crypto ipsec ikev1 transform-set AES-256-SHA
esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set TSET-3DES-SHA
esp-3des esp-sha-hmac
crypto map STATIC-MAP 10 match address
VPN-ROSARIO-CORDOBA
crypto map STATIC-MAP 10 set peer 200.69.0.1
crypto map STATIC-MAP 10 set ikev1
transform-set TSET-3DES-SHA
crypto map STATIC-MAP 20 match address
VPN-ROSARIO-TUCUMAN
crypto map STATIC-MAP 20 set peer 190.1.2.3
crypto map STATIC-MAP 20 set ikev1
transform-set TSET-AES-256-SHA
crypto map STATIC-MAP 20 set
security-association lifetime seconds 28800
crypto map STATIC-MAP 20 set
security-association lifetime kilobytes 4608000
crypto isakmp identity address
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication
pre-share
encryption 3des
hash sha
group 5
lifetime
10800
crypto ikev1 policy 20
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime
86400
crypto ikev1 policy 30
authentication pre-share
encryption 3des
hash md5
group 2
lifetime
86400
!
dhcpd address 172.16.0.10-172.16.0.250
invitados
dhcpd enable invitados
!
ssh 192.168.20.123 255.255.255.255 usuarios
ssh 192.168.10.0 255.255.255.0 servers
ssh timeout 30
ssh key-exchange group dh-group1-sha1
console timeout 0
management-access servers
username administrator password
iz7YVX.Y.ynPeumC encrypted privilege 15
tunnel-group 200.69.0.1 type ipsec-l2l
tunnel-group 200.69.0.1 ipsec-attributes
ikev1
pre-shared-key *****
tunnel-group 190.1.2.3 type ipsec-l2l
tunnel-group 190.1.2.3 ipsec-attributes
ikev1
pre-shared-key *****
!
class-map inspection_default
match
default-inspection-traffic
class-map NETFLOW-MAP
match
any
!
policy-map global_policy
class
inspection_default
inspect
ftp
inspect
tftp
inspect
ip-options
inspect
icmp
inspect
h323 h225
inspect
h323 ras
inspect
sip
class
NETFLOW-MAP
flow-export event-type all destination 192.168.10.14
class
class-default
!
service-policy global_policy global
Cryptochecksum:ecb96e45e3d142743591a2ba70c32519
: end
FW_Rosario#
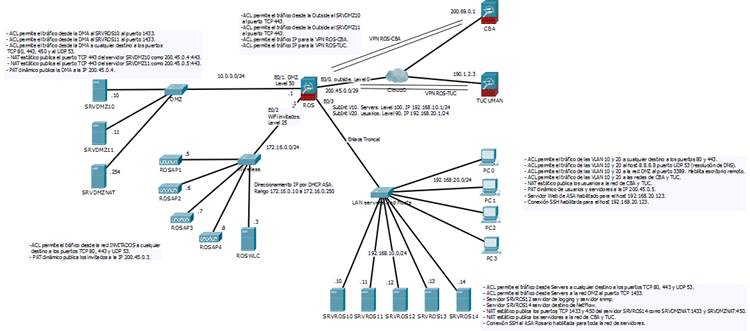
Resolución de Rodrigo Flores:
El trabajo realizado consta en relevar los names, los objetos, sus IP y comenzar a realizar un diagrama físico y lógico
donde a veces interviene mas la imaginación que los conceptos técnicos, la palabra es abstracción.
Resolución de Marcos Leiva:
La principal diferencia es la presencia de los dos ASA en failover.
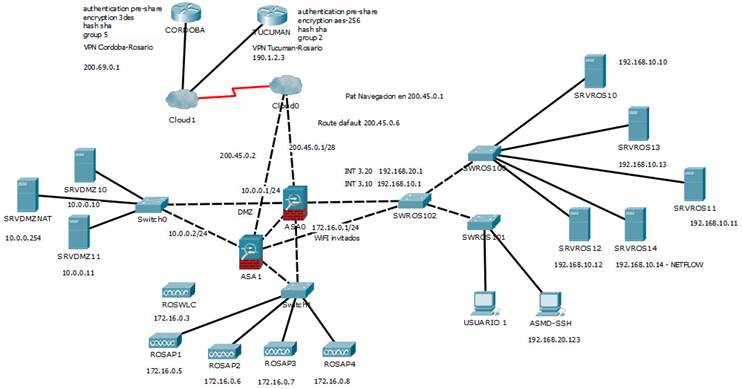
Las dos visiones de la red son diferentes pero similares al fín, se comprueba que no hay reglas estrictas en cuanto a documentación
pero lo imortante a transmitir es la cantidad de información útili que un layout puede proporcionar para un rápido troubleshooting.
(2016) IT Security may cause paranoid minds
Rosario, Argentina