Laboratorio de de
VPN tipo GRE para transportar tráfico OSPF, protegidas por IPSec
(tema extra curricular de CCNASecurity)
Fecha: 4de Agosto del2011 Instructor: Ernesto
Vilarrasa
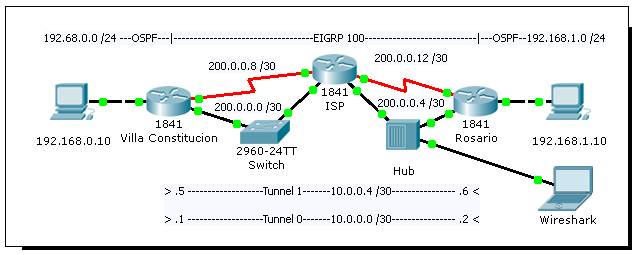
Escenario: en dos sitios remotos se ejecuta OSPF para la convergencia,
a travez de un ISP que posee un protocolo de
enrutamiento no compatible y no es una opción
redistribuirlos. El ambiente WAN, si bien es privado, debe considerarse
inseguro, protegiéndolo mediante IPSec.
La convergencia OSPF entre las dos redes se realiza
mediante el túnel GRE.

Villa Constitucion#sh run !hostname Villa Constitucion!!crypto isakmp policy 1(tunel 0) encr aes 256 authentication pre-share group 2!crypto isakmp policy 20 (tunel 1, pero podría utilizarse la misma policy) encr aes 256 authentication pre-share group 2 (DH: 1024 bits)crypto isakmp key Pr3Sh4redKeY address 200.0.0.6 no-xauth (tunel 0)crypto isakmp key Pr3Sh4redKeY address 200.0.0.14 no-xauth (tunel 1)!crypto ipsec transform-set ESP-AES-256-SHA esp-aes 256 esp-sha-hmac !crypto ipsec profile TUNEL set transform-set ESP-AES-256-SHA !interface Tunnel0
bandwidth 1024(definimos BW del
enlace, sólo es referencia para el costo OSPF: 10^8/BW[bps])
ip address 10.0.0.1 255.255.255.252
ip mtu 1400 (la MTU por defecto es
1500, pero se deben incluir las nuevas cabeceras GRE e IPSec)
tunnel source FastEthernet0/1 tunnel destination 200.0.0.6 tunnel protection ipsec profile TUNEL!interface Tunnel1 bandwidth 512 ip address 10.0.0.5 255.255.255.252 tunnel source Serial0/0/0 tunnel destination 200.0.0.14 tunnel protection ipsec profile TUNEL!interface FastEthernet0/0 ip address 192.168.0.1 255.255.255.0!interface FastEthernet0/1 ip address 200.0.0.1 255.255.255.252!interface Serial0/0/0 ip address 200.0.0.9 255.255.255.252 clock rate 125000!router eigrp 100 network 200.0.0.0 0.0.0.3 network 200.0.0.8 0.0.0.3 no auto-summary!router ospf 1 log-adjacency-changes network 10.0.0.0 0.0.0.3 area 0 network 10.0.0.4 0.0.0.3 area 0 network 192.168.0.0 0.0.0.255 area 0!end
ISP#sh running-config !hostname ISP!interface FastEthernet0/0 ip address 200.0.0.5 255.255.255.252!interface FastEthernet0/1 ip address 200.0.0.2 255.255.255.252!interface Serial0/0/0 ip address 200.0.0.10 255.255.255.252!interface Serial0/0/1 ip address 200.0.0.13 255.255.255.252!router eigrp 100 (no hay OSPF, ni túneles configurados) network 200.0.0.0 0.0.0.3 network 200.0.0.4 0.0.0.3 network 200.0.0.8 0.0.0.3 network 200.0.0.12 0.0.0.3 no auto-summary!end Rosario#show runn !hostname Rosario!crypto isakmp policy 10 encr aes 256 authentication pre-share group 2!crypto isakmp policy 20 encr aes 256 authentication pre-share group 2crypto isakmp key Pr3Sh4redKeY address 200.0.0.1 no-xauthcrypto isakmp key Pr3Sh4redKeY address 200.0.0.9 no-xauth!crypto ipsec transform-set ESP-AES-256-SHA esp-aes 256 esp-sha-hmac !crypto ipsec profile TUNEL set transform-set ESP-AES-256-SHA!interface Tunnel0 bandwidth 1024 ip address 10.0.0.2 255.255.255.252 ip mtu 1400 tunnel source FastEthernet0/0 tunnel destination 200.0.0.1 tunnel protection ipsec profile TUNEL!interface Tunnel1 bandwidth 512 ip address 10.0.0.6 255.255.255.252 tunnel source Serial0/0/1 tunnel destination 200.0.0.9 tunnel protection ipsec profile TUNEL!interface FastEthernet0/0 description Red Local ip address 200.0.0.6 255.255.255.252!interface FastEthernet0/1 ip address 192.168.1.1 255.255.255.0 duplex auto speed auto!interface Serial0/0/1 description Red Wan ip address 200.0.0.14 255.255.255.252 clock rate 125000!router eigrp 100 network 200.0.0.4 0.0.0.3 network 200.0.0.12 0.0.0.3 no auto-summary!router ospf 1 log-adjacency-changes network 10.0.0.0 0.0.0.3 area 0 network 10.0.0.4 0.0.0.3 area 0 network 192.168.1.0 0.0.0.255 area 0!end Verificación: Villa Constitucion#sh ip route Gateway of last resort is not set 200.0.0.0/30 is subnetted, 4 subnetsC 200.0.0.8 is directly connected, Serial0/0/0D 200.0.0.12 [90/20537600] via 200.0.0.2, 00:32:38, FastEthernet0/1C 200.0.0.0 is directly connected, FastEthernet0/1D 200.0.0.4 [90/284160] via 200.0.0.2, 00:32:38, FastEthernet0/1 10.0.0.0/30 is subnetted, 2 subnetsC 10.0.0.0 is directly connected, Tunnel0C 10.0.0.4 is directly connected, Tunnel1C 192.168.0.0/24 is directly connected, FastEthernet0/0O 192.168.1.0/24 [110/98] via 10.0.0.2, 00:07:56, Tunnel0 (Rosario) Villa Constitucion#sh crypto isakmp saIPv4 Crypto ISAKMP SAdst src state conn-id slot status200.0.0.1 200.0.0.6 QM_IDLE 1001 0 ACTIVE200.0.0.9 200.0.0.14 QM_IDLE 1002 0 ACTIVE ISP# sh ip route Gateway of last resort is not set 200.0.0.0/30 is subnetted, 4 subnetsC 200.0.0.8 is directly connected, Serial0/0/0C 200.0.0.12 is directly connected, Serial0/0/1C 200.0.0.0 is directly connected, FastEthernet0/1C 200.0.0.4 is directly connected, FastEthernet0/0 Rosario#show ip route Gateway of last resort is not set (no hay rutas estáticas quad zero definidas) 200.0.0.0/30 is subnetted, 4 subnetsD 200.0.0.8 [90/20514560] via 200.0.0.5, 01:04:07, FastEthernet0/0C 200.0.0.12 is directly connected, Serial0/0/1D 200.0.0.0 [90/284160] via 200.0.0.5, 01:04:19, FastEthernet0/0C 200.0.0.4 is directly connected, FastEthernet0/0 10.0.0.0/30 is subnetted, 2 subnetsC 10.0.0.0 is directly connected, Tunnel0C 10.0.0.4 is directly connected, Tunnel1O 192.168.0.0/24 [110/98] via 10.0.0.1, 00:07:55, Tunnel0 (Villa Constitucion)C 192.168.1.0/24 is directly connected, FastEthernet0/1 Rosario#show crypto isakmp saIPv4 Crypto ISAKMP SAdst src state conn-id slot status200.0.0.9 200.0.0.14 QM_IDLE 1002 0 ACTIVE200.0.0.1 200.0.0.6 QM_IDLE 1001 0 ACTIVE Paquetes capturados con Wireshark mediante el HUB en el enlace ISP-Rosario: 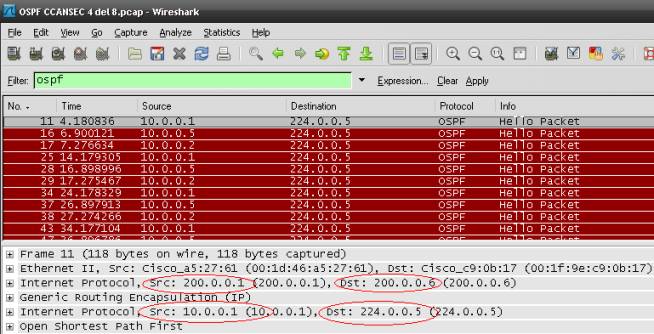
Advertir que se especifica el encapsulado GRE (Generic Routing Encapsulation) y sepuede leer info acerca del OSPF, origen y destinos de los túneles. 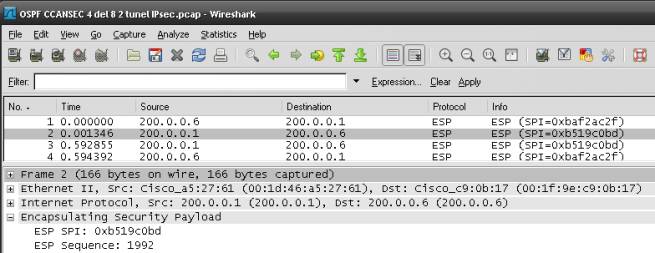
Paquete IPSec, ya no existe tráfico OSPF, sólo ESP (Encapsulation Security Payload), puedenCapturarse los paquetes EIGRP ya que NO esán protegidos, van por fuera del túnel. Con respecto a la convergencia de OSPF: en una fase de las pruebas, si bien el primer
túnel configurado se encontraba UP-UP en ambos extremos, no teníamos tráfico OSPF.Realizando una revisión en ambas configuraciones, encontramos diferencias de MTU en lasinterfaces Tunnel, ya que se deben reducir de 1500 bytes debido al reencapsulado delpaquete IP original en cabeceras GRE, mas el encabezado ESP, etc...Si ambas interfaces no tienen el mismo MTU, OSPF no converge. Mas datos: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080093f0d.shtml (2011) Pretty girls in the beach don´t speak about networking.
Rosario, Argentina